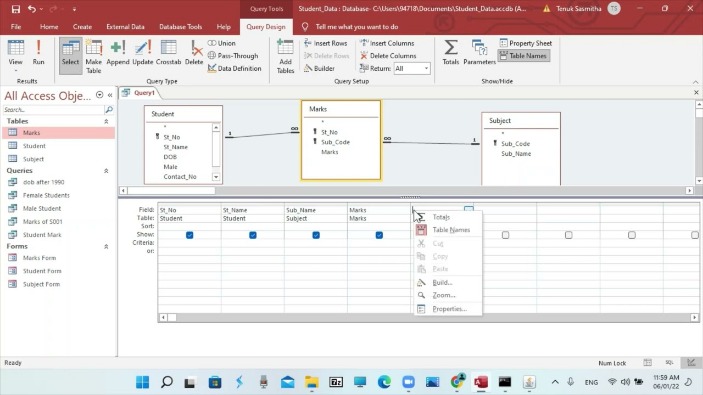
This helps obscure the origin of the data (and makes it hard for anyone to find your IP address). Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing. The Tor network combined with a VPN is one of the safest ways to get on the dark web. Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity. Tor shares similarities with VPNs and proxy servers — all of these tools allow anonymous browsing.
It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. The deep web is just the part of the internet you can’t find with a search engine. When you search for something on Google or Bing, you’re using the clear web. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily.

This is partially thanks to its SmartPlay feature, which automatically switches your DNS server when you try to access geo-restricted content. This negates the need to download, install, and run the Tor browser separately, and lets you access the Tor network without your ISP knowing. NordVPN has a huge worldwide network of RAM-only servers and high standards of both privacy and security. Let's take a closer look at the best VPNs you can use to safely access the dark web. The right VPN can make accessing the dark web seem a little less intimidating.
Methodology For Choosing The Best VPN For Safely Accessing The Dark Web
Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. People mostly use it for covert communication, anonymous tips submission, and stuff like that. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web.
HTTPS-only
The anonymity provided by onion routing comes at the cost of slowing your internet considerably. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. In the same spirit, the Central Intelligence Agency (CIA) established a .onion site to help people access its resources worldwide anonymously and securely. However, data is required for understanding, monitoring, and improving the network. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data.
Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features. In 2018, someone gained access to a third-party data center in Finland. While connected through NordVPN, your internet traffic is protected using AES 256-bit encryption.
Types Of Cyber Threats On The Dark Web
- Although the surface web only comprises about 4-5% of the entire internet, scope is important to keep in mind because this is still impressively expansive.
- You should avoid downloading files via Tor to maximize your anonymity.
- Arguably, the best-known tool used to access the dark web is the Tor Browser.
- When you connect to the internet using Tor, your data goes through multiple phases of encryption before it’s directed through a random series of servers called ‘nodes’.
- Using a reputable Virtual Private Network (VPN) or a secure proxy can help mask your IP address and encrypt your traffic before it even reaches the Tor entry node.
This guide provides clear, step-by-step instructions to safely explore the Dark Web using Tor, helping you stay protected, informed, and anonymous. But navigating the dark web is full of cybersecurity and legal challenges. It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime. Accidentally downloading or viewing illegal materials may result in severe legal consequences. Clicking on links there might take you to illegal or harmful material without warning. The dark web is full of unknown and potentially dangerous content.
This may be welcome news to those in states where security services have attempted to block ‘anonymous’ email websites like these from the open web. For maximum security users should only access sites with the .onion suffix via the browser. Engaging in illegal activities—like buying drugs, trafficking stolen data, or distributing harmful content—is absolutely against the law.
- For a number of technical reasons, it’s much faster and more reliable than Tor.
- It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services.
- The dark web might sound like a mysterious part of the internet, and in many ways, it is.
- Tor routes data through multiple volunteer-operated servers, or “nodes,” disguising the original IP address and location.
- The dark web contains a range of content, some of which is illegal, including marketplaces for drugs, weapons, stolen data, and other illicit services.
Our Network
The looming threat of quantum computing has sparked adoption of post‑quantum cryptography in anonymity networks. As of early 2025 the reboot remains online, though it commands a fraction of its former traffic and faces constant DDoS attacks and phishing clones. Adopt a skeptic’s mindset—question every download, every prompt and every request for information—and you’ll shrink the attack surface that criminals and investigators alike rely on to unmask careless users. Operational security, or OPSEC, is the discipline that turns technical anonymity into real‑world protection. SecureDrop and similar onion services give insiders a safe conduit to expose corruption or safety lapses without risking employer surveillance. Technically unindexable by surface‑web crawlers; directory lists exist only within the network
Search engines cannot reach these pages, and directories inside the network list them only sporadically, reinforcing a culture of anonymity. Sites use nonstandard domain suffixes such as “.onion” and route traffic through multiple encrypted relays, obscuring both the server’s location and the visitor’s IP address. Because its sites are openly linked, the surface web represents only a small fraction of total online content, but it feels vast because it is the most visible. You’ll learn how it differs from the surface and deep webs, how Tor and similar networks maintain anonymity, and why some activities cross legal lines.
What Is APKPure And Is It Safe To Use On Android?
Internet shutdowns affected 4.78 billion people in 2024 alone, as governments from Iran to Myanmar throttled access during protests and elections. Excluded from search engines by design (robots.txt, login barriers) Multi‑layer encryption obscures both server and user locations, fostering strong anonymity Predominantly legal, routine activities (banking, corporate dashboards, academic journals) Requires Tor, I2P or similar anonymity tools; not reachable via conventional browsers
What Is The Onion Network?
Fortunately, it’s not a criminal offense if you simply search the dark web, but if you use it to carry out illegal activities, you get in trouble. Privacy and anonymity are the core values of the dark web, and it hosts both harmless activities and illegal content. This is where Tor websites are located, deemed the ‘dark web,’ and can only be accessed by an anonymous browser. The dark web isn’t only about illegal activities; its primary purpose is to provide maximum anonymity by making your connection private online through encrypted servers.
Is It Illegal To Use The Tor Browser?
The dark web is notorious for hosting marketplaces that deal in illegal goods and services, such as drugs, weapons, counterfeit money, stolen data, and even human trafficking. Because VPNs offer users anonymity and mask their actual location, they’re also effective tools for accessing geo-locked services. The difference between the surface web and the deep web is that pages, websites, and content on the deep web are only accessible to authorized users with the appropriate credentials. The dark web is the part of the internet where users can access unindexed web content anonymously through special web browsers like The Onion Router (Tor). Tor provides anonymity through a process known as “onion routing,” where internet traffic is encrypted and passed through multiple network nodes. Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites.
All anyone monitoring your browsing habits can see is that you're using Tor. My work bridges the gap between technology and cybersecurity education, helping to inform and empower others in the ever-evolving cyber landscape. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape.
It is worth noting that the dark web is not always illegal, as many activities take place on the dark web that are within the law. The dark web has several anonymity layers, making it difficult to access. The deep web includes both legal and illegal content, including the portion known as the dark web.
The dark web is a subset of the deep web that is intentionally hidden and requires specialized tools such as Tor, I2P, or Freenet. The dark web is not meant for the general public since it is harder to access and need technical knowledge. These corners are deliberately concealed from the public eye and require specialized tools and browsers to access, making it more difficult for the average person to explore.
Most threats don’t come from the network itself — they come from the sites you visit, the files you download, and the mistakes you make. A VPN doesn’t encrypt traffic after it exits the Tor network. Your internet activity is still subject to exit node risks, so always use HTTPS and avoid entering any personal information on unencrypted sites. That means your ISP only sees encrypted VPN traffic and can’t tell you’re using Tor. Don’t download anything unless you’re absolutely sure it’s safe.
However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups. There are many legitimate uses for dark web services and communication. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). Drugs, weapons, and stolen IP and data are all hot businesses on the dark web, with terabytes of information on offer. When the dark web is mentioned online, it is usually in tandem with criminal marketplaces and arrests made by law enforcement agencies.



