
Instead, I2P uses its own brand of hidden sites called “eepsites”. Unlike Tor, however, it cannot be used to access the public internet. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. A VPN, in combination with Tor, further enhances the user’s security and anonymity. That information is hidden simply because most users won’t find it relevant. Put simply, the deep web is all the information stored online that isn’t indexed by search engines.
The inherent anonymity of the place attracts scammers and thieves, but what do you expect when buying guns or drugs is your objective? “Bitcoin has been a major factor in the growth of the dark web, and the dark web has been a big factor in the growth of bitcoin,” says Tiquet. As a result, “The quality of search varies widely, and a lot of material is outdated.” The anonymous nature of the Tor network also makes it especially vulnerable to DDoS, said Keeper’s Tiquet. In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers.
Unlike overt seizures, Dream’s shutdown was an exit by administrators, a pattern sometimes seen when market owners bail out. In effect, Operation Bayonet simultaneously shut down both markets, netting thousands of criminals and shattering community trust. In practice, authorities combine blockchain forensics, metadata analysis and international raids to dismantle these sites. Unlike the deep web private or unindexed pages, the dark web specifically refers to sites requiring special software Tor to access.
Every security tip known to me is shared as well. We’re back with another video in our Webz Insider video series on everything web data. Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI. By submitting you agree to Webz.io's Privacy Policy and further marketing communications. Freshtools has some characteristics that help it stand out from the other dark web stores.
- Cypher marketplace has been on the list of the best dark web shops for a while and deals with the business of a variety of products and services.
- Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web.
- It is entirely focused on financial cybercrime and offers much more than just stolen cards or basic logins.Here you will find malware logs, remote access (RDP), brute force accounts, complete identity packages, and access to financial platforms.
- As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.
- You won't find drugs here, but you will find tons of credentials, RDP access, CVVs, and records stolen using malware.The platform works with data collected by well-known malware such as Lumma, RedLine, Raccoon, Vidar, and Aurora.
What Is The Safest Way To Access Darknet Markets?

While they look like your run-of-the-mill websites, there are important differences. While it provides anonymity for privacy advocates and whistleblowers, it’s also a breeding ground for cyber threats. Hidden, encrypted and out of reach of traditional search engines, the dark web is a place where anonymity rules. It is notorious for illegal transactions and activities such as drug trafficking, arms dealing and identity fraud. The dark web is a section of the Internet not searchable through traditional search engines, where privacy and anonymity reign. Beneath it lies the deep web and, further still, the dark web – a hidden network often shrouded in mystery, speculation and misinformation.

While these hidden networks can be used for legitimate purposes, they are equally significant as vectors for cybercrime and illicit activities. Companies must implement strong data security measures, employ encryption, and monitor for data breaches to protect customer and employee information. Personal and financial data are commonly sold on dark markets, facilitating identity theft and fraudulent activities. Dark markets continually adapt and evolve to stay ahead of law enforcement and security measures. Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy.
Top Darknet Markets
For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that. If you want to improve your security further, you could also use a VPN at the same time as Tor. It's a free-to-use web browser based on Firefox that lets you access the dark web relatively safely. In this guide, we'll show you what you need to know about how to access the dark web and how to keep yourself safe while you use it. In short, WTN continues to grow as a highly targeted and resilient marketplace within Canada’s dark web scene.

#1 Install A VPN
This English-language DNM sold drugs, data, and counterfeit items. DNMs have a limited life and may be shutdown suddenly, leaving users with unfulfilled orders and sellers with no means of communication. As the DNM builds a small pool of users and sellers, it will snowball into a lucrative operation IF the service remains reliable and secure. The site admins must market the DNM, usually on dark web forums. Once the website is coded, the policies created, the admins ready, and the hosting secured, the site goes live on the TOR network. They list their products or open an online “store”.
Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. Darknet markets facilitate transactions for illegal goods and services. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information.
#7 Can I Use Other Browsers Except Tor To Access Darknet Markets?

These hidden markets promise anonymity, but in practice, users often slip up. Law enforcement agencies actively monitor these markets and can track users despite anonymity measures. Dark markets are online platforms on the darknet where illegal goods and services are traded. Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’. This browser enables access to websites with .onion domain extensions, which are specific to the Tor network. Accessing darknet markets can be risky, and it is important to take precautions to protect your privacy and security.
Research Reports Download Report
Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. The deep web is basically all the content that you can’t find using Google or Yahoo search. In addition, the content on the pages don’t need any special or custom configuration to access. So, even though it does exist on the internet, Google doesn’t index any of these pages or content. Google considers the majority of the content on the entire web highly irrelevant and useless to its users.
Due to its absolute anonymity for knowledgeable users, the chance of running into bad people is also realistic, as they can operate relatively freely without the fear of getting caught doing something unlawful. In opennet mode, the network will automatically assign you to other users on Freenet’s network. Freenet is similar to I2P – you can only connect to sites within Freenet’s own network. Meanwhile, Facebook also offers dark web access to their social network. Well-known news websites, such as ProPublica, have launched deep websites.

Dark Web Links: The Best Onion And Tor Sites In 2025
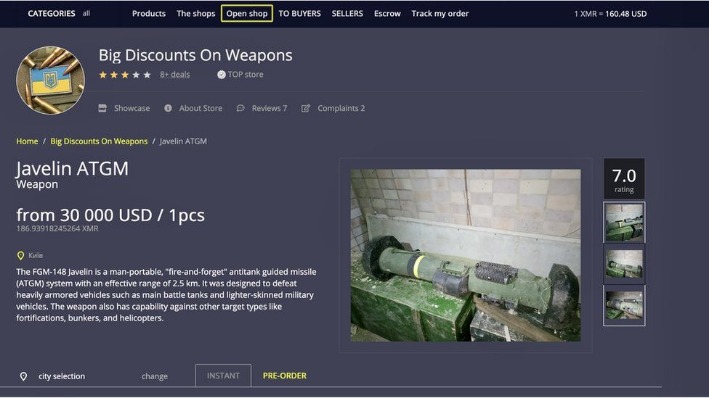
For those venturing to the shadier side of the web or those who just want to know their identity is safe, dark web monitoring tools and identity theft protection are a must-have. Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware. Dark web browsers and search engines do a lot of work to mask user identities, but you’re never completely untraceable.
The Full List Of Trusted Darknet Markets:
It’s occupied by people from all walks of our complex and layered lives – from outright criminals and troublemakers, to journalists, dissidents, and security researchers (like myself). The darknet is not just a domain for illicit activities, it also serves as a space that offers unparalleled opportunities for discourse, free market trade, and collective and communal discovery. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. This can include medical records, research papers, private forums, and networks. The deep web is content that search engines such as Google do not index. Simply accessing the dark web and using the Tor browser may already raise government suspicion.
Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you're looking for. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Part of what makes the dark web the dark web is that you can't access it through your normal web browser, nor can you look something up on it via a Google search. The dark web comes with its own set of tools and services, including web browsers and search engines (which I'll get on to in a moment).
These lists are curated based on user feedback, uptime, and overall reputation, making them indispensable tools for navigating the darknet landscape. Buyers benefit from access to a broader selection, ensuring they can find exactly what they are looking for. These platforms rely on advanced encryption and decentralized systems to ensure anonymity and reliability for both buyers and sellers.
Conclusion: Access The Dark Web Safely And Responsibly
Well, it’s really not that complicated – using the Tor over VPN method means connecting to a VPN service before using the Tor browser. This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP.
The Tor browser is a free, open-source software that allows you to browse the internet anonymously and access the dark web. To make a purchase on a darknet market, you will need to fund your account with cryptocurrency, such as Bitcoin or Monero. In addition to these common scams, users should also be aware of “Bitcoin scams.” These scams can occur when users are buying or selling Bitcoin on the Darknet market.



