
This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. These browsers have tracking technologies that compromise anonymity. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny.
Digital Rights And Advocacy Groups

Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Although it’s no longer active, it’s setting the standard for coming onion links.
How To Browse The Dark Web Legally
We will not be discussing illegal activities or providing instructions that could enable them. Direct access to services hosted on the Dark Web is beyond the scope of this article. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
Why Use Tor For Accessing The Dark Web?
The Mailpile .onion site can download information anonymously from any server or web service like Gravatar. It aims to preserve the internet’s scientific and cultural heritage. While this is not much compared to standard email services, it is enough for PGP-encrypted messages. The downside is that it limits data to only 25mbps per user. SecMail is one of the most popular email services on the dark web.
Ethical Considerations And Risks
Besides, victims of crime may want to hide their identities from their perpetrators. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. The system is designed to provide enhanced security and privacy features. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser.

However, accessing actual dark web services linked from those subreddits requires specific tools. Dark web sites are hosted on overlay networks that require specialized software and configurations for access. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet.
Tools Needed For Safe Access
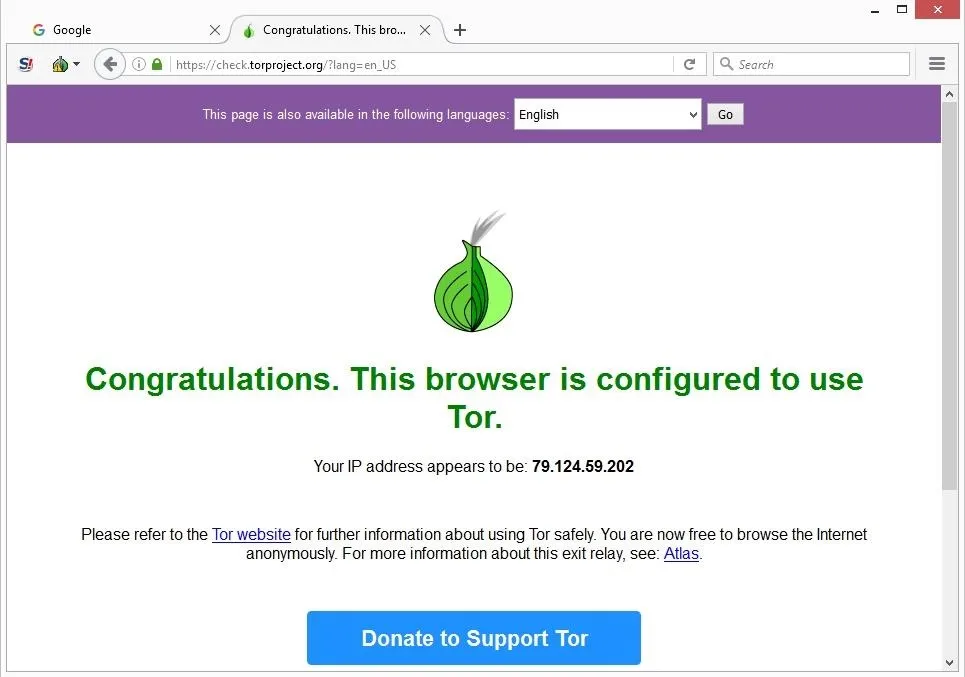
While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. Instead, you need to get the Tor browser to access the dark web. It’s impossible to access the dark web with a regular browser like Chrome or Safari. That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy.
- Other sites explicitly block search engines from identifying them.
- ProPublica covers all the controversial stories from corrupt politicians, child labor, etc., in English and Spanish.
- It's not like you can type every random collection of links you think and search, considering most of them are down.
- And remember the focus is on learning and understanding, not participating in anything illegal or unethical.
- Actually let me explain, everywhere the dark web (not deep web) is described as some notorious place that has all these absolutely mind-blowingly illegal things.
I2P can only be used to access hidden sites that are only available on the I2P network. Your ISP can’t see which websites you’re visiting on the dark web when you’re using Tor, but they might be able to predict or assume you are using Tor if they analyze your monitored internet traffic. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites.
Safe Browsing
This .onion site is a bit different from the others reviewed above. The .onion site has thousands of downloadable comic books ranging from niche to mainstream. Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol.
Step 2: Download Tor Browser
Hyphanet (formerly Freenet) is another anonymous network that allows you to share and retrieve information without censorship. I2P (Invisible Internet Project) is an open-source network designed to allow anonymous and private communication. Each of these options offers unique privacy features, with Whonix and Qubes for higher security setups, and Kodachi and Liberté for portability. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
Step 2: Download And Install Tor Browser
H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be. Unlike Tor, which focuses on accessibility to the “open” web through exit nodes, I2P is geared toward creating hidden, anonymized websites and services within its own ecosystem (called “I2P sites” or “eepsites”). A network browser gives you access to sites with the ‘.onion’ registry operator. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.

MacOS users will need to drag and drop the Tor Browser icon to the Applications folder. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. Now that you’ve completed the download, it’s time to install the Tor browser on your device.
When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. The dark web is a decentralized web, which means that the data is stored on many different servers around the world.
The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites. Once you have the Tor or Onion Browser downloaded and are connected to the Tor network, you can browse the dark web by visiting .onion links — dark web sites that are accessible only via the Tor network. It's a place where you'll find data leaks and illegal trades, but also legitimate, legal online activities users want to carry out without attracting the attention of law enforcement agencies or governments. It’s essential to approach these communities with a strong understanding of cybersecurity principles, responsible online behavior, and the legal implications of accessing and discussing illicit content. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers.



