
Copy the .onion link carefully to avoid mistakes, as typos can lead to error pages or potentially malicious sites designed to impersonate the Hidden Wiki. This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted. While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. Daniel’s Hosting specializes in anonymous hosting services optimized for Tor sites, providing secure environments and DDoS mitigation. The ProtonMail Onion site offers the same encrypted email services trusted globally, now accessible anonymously through Tor.
Encrypted Communication Tools
- It’s divided into commercial links (from crypto services to gambling sites) and non-commercial links (like social media).
- One should always be wary when exploring this part of the web, as engaging with certain contents can lead to serious legal consequences.
- All content published here is for educational purposes only.
- One of the key recommendations is to use a reputable VPN (Virtual Private Network) to mask your IP address, ensuring that your online activities remain private.
- To navigate this realm safely, users must be aware of the importance of a secure connection, ensuring that their adresse dark web experience remains private and protected.
If you decide to enter the dark web, always make sure to take all the necessary online privacy precautions. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. Simply accessing the dark web and using the Tor browser may already raise government suspicion.

Well, now it’s time to fire up Tails and do a little bit of tinkering. For this tutorial, I’ve used Universal. I recommend using a stick since DVDs have a read-only function after you’re done burning well and accessing the dark web required a bit of writing.
Use A Unique Email Address For Different Platforms
It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Sites in the dark web have .onion as their domain in their URLs. You can also use Brave to access the dark web on your computer. This will protect your privacy and add another layer of security, keeping your browsing private from your ISP, cyber attackers, and other third parties.
Welches Ist Das Beste VPN Für Das Dark Web?
While some studies have claimed that illegal Bitcoin activity is as high as 44%. These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. Last but not least, we here at Pixel Privacy never condone illegal activity.

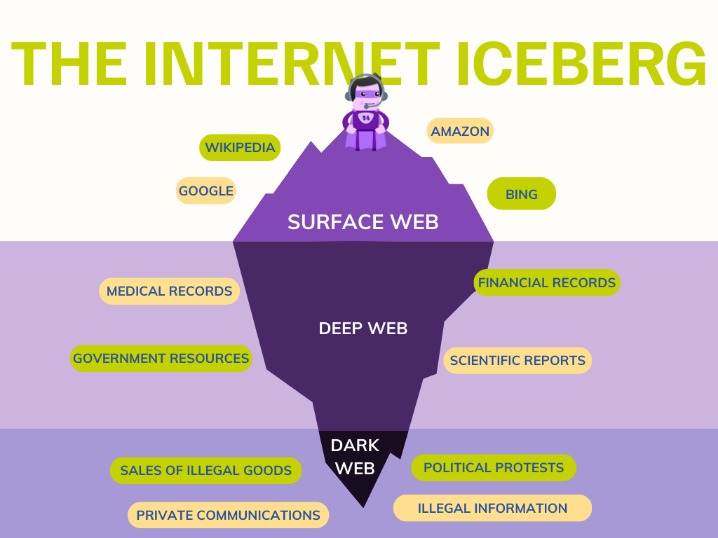
If one of those platforms suffers a data breach, your email address could be exposed and end up on the Dark Web. If you fall victim to a phishing attack and unknowingly provide your email address to the attackers, they may sell or use it on the Dark Web, exposing you to potential risks. It is crucial to take proactive measures to protect your online identity and remove your email address from the Dark Web. This information can be used to target ads and monitor your internet usage. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. This can include medical records, research papers, private forums, and networks.
- There are multiple search engines on the dark web that can help you find what you’re looking for.
- Fraud alerts are free and can provide an additional layer of protection while you address any potential identity theft issues.
- If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.
- It hosts a variety of content types, each serving different purposes and attracting diverse audiences.
- Enabling two-factor authentication (2FA) adds an extra layer of security to your email account, making it more difficult for unauthorized individuals to access your account.
#1 Install A VPN
The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites. If you want to buy something on the dark web, it’s a best practice to create a fake identity. Start the Tor browser by double-clicking on “Start Tor Browser” (for Windows) or “TorBrowser” (for Mac users). MacOS users will need to drag and drop the Tor Browser icon to the Applications folder.
Is The Hidden Wiki Safe?
For developers and site operators, hosting on the dark web requires privacy, uptime, and resistance to attacks. These services form the communication backbone for sensitive conversations in high-risk environments. For real-time messaging, Ricochet Refresh offers decentralized, peer-to-peer encrypted chats over Tor without central servers, greatly reducing surveillance risks. Sigaint provides encrypted email favored by whistleblowers and privacy advocates, focusing on ease of use and robust security.
Recommendations For Safe Browsing
As when visiting ordinary websites, stay alert to security risks on onion sites. This hidden part of the internet, often characterized by anonymity and the presence of illegal activities, requires careful navigation to protect your identity and personal information. While the dark web offers anonymity and access to sites cachés, users must be aware of the implications and risks involved in their exploration. Utilizing these search engines can greatly enhance the experience of browsing the dark web, making it more accessible to users seeking specific content. A VPN is often recommended to protect users’ identities and enhance their security while exploring content in this hidden part of the internet. It represents a hidden part of the internet that isn’t indexed by traditional search engines, making it accessible only through specific software and configurations.
FAQ: More About Onion Sites
It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. Wondering what the best dark web VPN to use with Tor is for accessing the best onion sites on the dark web?
Alt Address
Start by immediately securing your compromised accounts with strong, unique passwords and enabling two-factor authentication. One effective tool to mitigate these dangers is AdGuard Temp Mail, a service designed to provide disposable email addresses that protects your primary account. When your email appears on the dark web, it exposes you to risks like phishing, spam, and other cyber threats.
Many people install a VPN as well, but then you're putting your trust in an additional third party to not track your activities or report them to anyone else. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn't know exactly what you're doing. Even with Tor and onion routing in place though, you're not suddenly completely invisible and free to do whatever you want, without repercussions. It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web. You'll often see these terms used in your travels across the internet, and there's some confusion about what they mean.
By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. These browsers have tracking technologies that compromise anonymity. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. Think of it as the internet’s wild card.



